With the rise in cybercrime and the increasing sophistication of hackers, it has become more crucial than ever to protect our digital identities. Gone are the days when a simple password was enough to safeguard our online accounts. Enter multi-factor authentication (MFA), a security measure that combines multiple layers of verification to ensure only authorized individuals gain access. But does MFA really live up to its hype? In this article, we delve into the world of MFA, exploring its effectiveness in protecting against unauthorized access and examining whether it is truly worth implementing.
Importance of secure authentication methods
In today’s digital age, where cyber threats are becoming increasingly sophisticated, ensuring secure authentication methods is of paramount importance. With the rise in data breaches and hacking incidents, organizations and individuals alike need to take proactive measures to protect their sensitive information. Implementing secure authentication methods not only provides an extra layer of protection but also helps prevent unauthorized access to accounts and systems.
One important aspect of secure authentication methods is multi-factor authentication (MFA). MFA combines two or more different types of credentials to verify a user’s identity, making it significantly harder for attackers to gain unauthorized access. By requiring multiple factors such as passwords, biometrics, security tokens, or SMS codes, MFA adds an additional level of security that complements traditional usernames and passwords. This reduces the risk associated with single-factor authentication methods that can easily be compromised through brute force attacks or stolen credentials.
Furthermore, secure authentication methods help instill confidence in users that their personal information is being protected. As users become more aware of the potential risks online, they are less likely to engage with platforms that do not prioritize security measures. By implementing strong authentication protocols such as encryption techniques or adaptive access controls, organizations can demonstrate their commitment to safeguarding user data and build trust among their customer base.

What is multi-factor authentication?
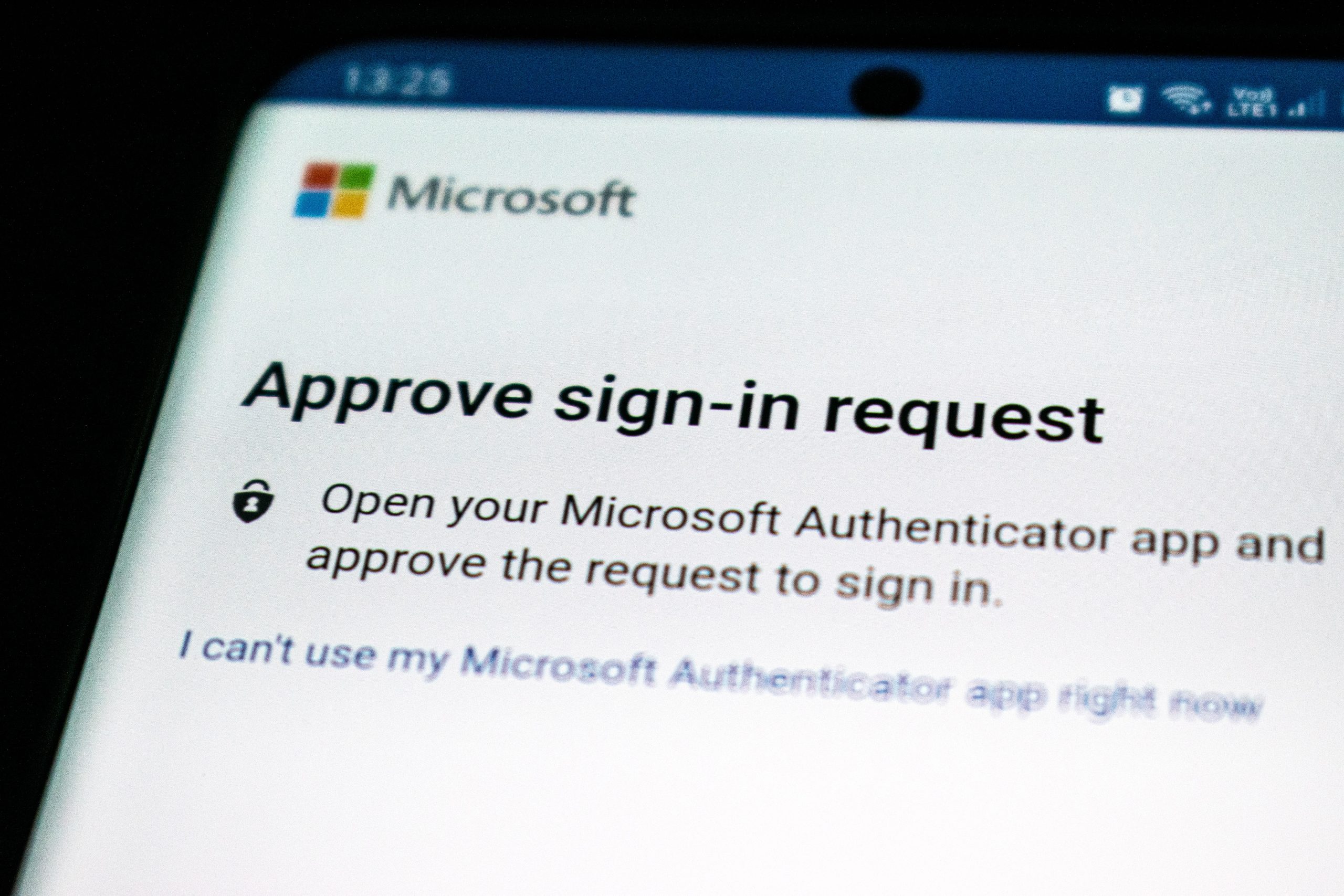
Multi-factor authentication (MFA) is a security measure that adds an extra layer of protection to online accounts. Instead of relying solely on a password, MFA requires users to provide multiple pieces of evidence before granting access. This evidence typically includes something the user knows (such as a password), something they have (like a unique code sent to their mobile device), and something they are (biometric data like fingerprints or facial recognition).
The goal of multi-factor authentication is to make it significantly more difficult for hackers to gain unauthorized access to sensitive information. Even if a cybercriminal manages to obtain someone’s password, they would need additional factors such as the physical possession or biometric characteristics associated with the account. By using this layered approach, MFA helps protect against common attacks like phishing, brute force attempts, and credential theft.
While multi-factor authentication significantly enhances security by making it exponentially harder for hackers to breach accounts, it is not foolproof. There are still vulnerabilities that attackers can exploit, such as sim swapping or social engineering tactics used to trick individuals into revealing their credentials over the phone. However, when combined with other best practices like regular updates and strong passwords, MFA becomes an indispensable tool in safeguarding personal information online.
Benefits of multi-factor authentication
One of the key benefits of multi-factor authentication (MFA) is its ability to provide an additional layer of security to protect user accounts from unauthorized access. While traditional password-based authentication can be easily compromised through various means, MFA adds a second or third factor, such as a fingerprint scan or a unique code sent to a user’s mobile device, making it significantly more difficult for attackers to gain access.
Another advantage of MFA is that it helps mitigate the risks associated with weak passwords. Many users tend to choose simple and easily guessable passwords, leaving their accounts vulnerable to brute force attacks. By adding an extra layer of authentication, even if an attacker manages to obtain the password, they will still need physical possession of the second factor (e.g., a smartphone), which significantly reduces the likelihood of successful unauthorized access.
Furthermore, multi-factor authentication has shown great potential in protecting against phishing attacks. Since MFA requires additional verification beyond just entering login credentials on a suspicious website or app, it becomes much harder for attackers to deceive users into providing their personal information. The added complexity and layers provided by MFA serve as effective deterrents for potential phishing attempts.
Overall, multi-factor authentication offers several significant benefits that make it an essential tool in securing online accounts and protecting personal data from cybercriminals. Its ability to add extra layers of security and mitigate various vulnerabilities associated with traditional password-based systems positions MFA as a highly effective solution in today’s digital landscape.

Limitations and challenges of multi-factor authentication
One of the limitations of multi-factor authentication (MFA) lies in its reliance on various factors, such as passwords, biometrics, and tokens. While this approach enhances security by requiring multiple forms of verification, it also introduces complexity for users. Remembering multiple passwords or carrying physical devices can be burdensome and frustrating for individuals who need to authenticate frequently across different systems or platforms. This inconvenience may lead to user resistance or non-compliance with MFA policies, ultimately undermining its effectiveness.
Another challenge is the potential vulnerability in the implementation of MFA protocols. An improperly configured MFA system can create loopholes that malicious actors can exploit. For instance, weak storage practices of authentication data or a faulty integration with other technologies could expose weaknesses in the overall security framework. To address these challenges, rigorous testing and continuous monitoring are essential to identify any vulnerabilities before they become exploitable threats.
In conclusion, while multi-factor authentication is an effective means to enhance security, it is not without limitations and challenges. The burden placed on users to remember multiple credentials and the potential vulnerabilities introduced by improper implementation are factors that must be addressed when implementing an MFA solution. By acknowledging these issues and working towards mitigating them effectively, organizations can maximize the benefits of multi-factor authentication without compromising user experience or leaving their systems exposed to threats.
Case studies: success stories and failures
When it comes to multi-factor authentication (MFA), case studies provide valuable insights into both success stories and failures. On the success front, companies like Google have set an impressive track record. By implementing MFA through their authenticator app, they achieved zero reported account hijackings among their employees. This showcases the effectiveness of MFA in thwarting unauthorized access attempts by adding an additional layer of security beyond just usernames and passwords.
However, not all stories end on a triumphant note. One prominent example is Reddit’s failed attempt at implementing SMS-based MFA. In 2018, it was revealed that hackers managed to bypass this form of authentication and accessed users’ accounts by intercepting text messages containing verification codes. This unfortunate incident demonstrates the vulnerabilities of relying solely on SMS as one factor for authentication, which can be exploited by sophisticated attackers.
These case studies emphasize that while MFA can be an effective security measure if properly implemented, it is crucial to understand the limitations and potential risks associated with different factors used in the process.
Comparison with other authentication methods
While multi-factor authentication (MFA) offers enhanced security, it is important to compare it with other authentication methods to understand its effectiveness. One commonly used method is the traditional username and password combination. However, this method has proven vulnerable to hacking attempts, as users often choose weak passwords or reuse them across different services. MFA adds an extra layer of security by requiring additional factors such as a fingerprint scan or a one-time passcode, reducing the likelihood of unauthorized access even if the password is compromised.
Another authentication method gaining popularity is biometric authentication, which uses unique physical characteristics like fingerprints or facial recognition for identification. Biometrics are difficult for attackers to replicate and provide a high level of security. However, biometric data can be stolen or manipulated in some cases, raising privacy concerns compared to MFA that does not rely on personal biological features. Consequently, MFA strikes a balance between convenience and security by offering multiple layers of protection without relying solely on biometrics.
In conclusion, while traditional username and password combinations may be convenient for users due to familiarity, they lack robustness against hacking attempts compared to multi-factor authentication (MFA). Biometric authentication offers higher levels of security but raises privacy concerns due to the use of personal biological features. MFA provides enhanced security without overstepping boundaries related to privacy concerns associated with other methods while maintaining ease-of-use for end-users through various forms such as two-step verification using SMS codes or push notifications on mobile devices.
Conclusion: Overall effectiveness of multi-factor authentication
In conclusion, multi-factor authentication has proven to be highly effective in enhancing the security of online accounts and systems. By requiring multiple forms of verification, such as a password, fingerprint scan, or one-time code sent to a mobile device, it significantly reduces the likelihood of unauthorized access. Not only does this provide an additional layer of protection against cyberattacks and data breaches, but it also offers peace of mind to users who want to ensure their personal information remains secure.
Furthermore, multi-factor authentication addresses the vulnerability inherent in relying solely on passwords. With the prevalence of password leaks and brute force attacks, it has become increasingly clear that passwords alone are not enough to protect valuable digital assets. Multi-factor authentication offers a more robust defense strategy by adding complexity and diversity to account security measures. This reduces the chances that an attacker will be able to bypass all layers and gain unauthorized access.
Overall, while no security method is foolproof, multi-factor authentication has consistently demonstrated its ability to enhance the effectiveness of traditional single-factor methods like passwords. Its combination of convenience for users and heightened security measures make it an essential tool in today’s ever-evolving threat landscape. As technology advances and cybercriminals become more sophisticated in their tactics, adopting multi-factor authentication should be a priority for individuals and organizations looking to safeguard their sensitive information.